
Personal computer taken to a company help desk, humans + horses


Personal computer taken to a company help desk, humans + horses


Hundreds of gigabytes of horse porn, right in a folder on his desktop called “horse”. The thumbnail of the folder made it incredibly clear what the folder was and what was in it, which was made extra clear by the max zoom his desktop icons were set to. (it was like, no joke, almost 1/10th the screen).
Fun fact: that was the day I learned my state doesn’t have mandatory reporting laws for animal abuse, only csam.


I think it’s one of those things that is against the spirit of a law but not the letter of it. It feels illegal, it probably should be illegal, it might be illegal in the future, but for now it’s sketchy but technically above board.


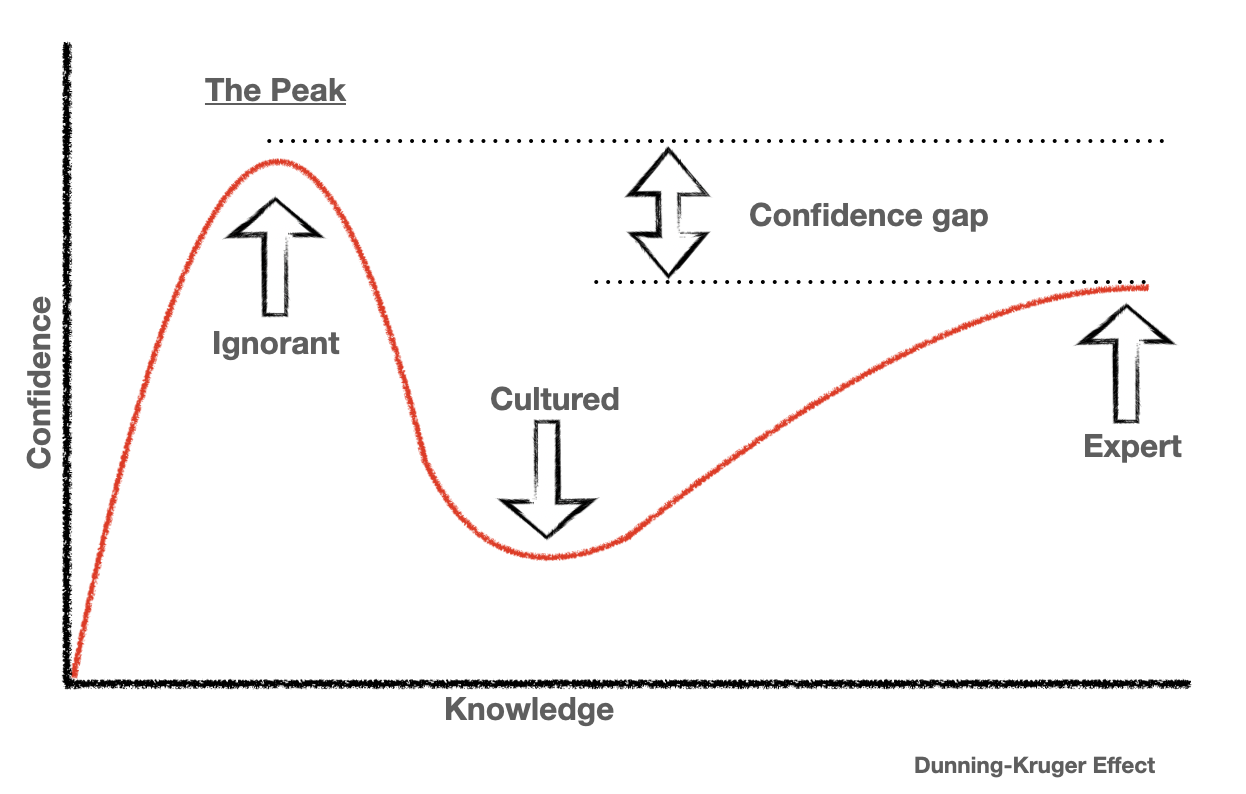
The thing about rational actors, is when given the same information they should make the same choices. I would argue that they’re most likely, instead, just at the peak of mt. stupid


We shouldn’t blame the victims that society failed to properly educate. You’re right that if people intimately understood apple the way you probably do, they’d never buy an apple product. I would argue, however, that it’s a failing of education not an informed choice to be corporately cucked.


TL/DR he wants to move the touchback to the 35


Noooo, you got this backwards. Think about how many times you wanted an extra key for something. Push-to-talk in VoIP apps, extra modifier keys so you don’t have to use double-modifiers… The possibilities are endless!
Standardize more useless keys so I can remap them on every keyboard!


It 100% is part of the character; so is the accent if you didn’t know. He speaks a perfect Midwestern accent when not in character


I don’t think anyone should expect a battery replacement to be free after 10 years, but it shouldn’t cost $100,000
Just because you can’t use it doesn’t mean a hacker can’t. If someone discovered a vulnerability in the 3g handshake or encryption protocol, it could be an avenue for an RCE.


I guess I should rephrase.
I label a lot of boxes and spice containers but nothing unhinged lol


deleted by creator


DYMO Embossing Label Maker
They’re like $9 on Amazon and I label everything. I have 2 myself, and they’re also my go-to for white-elephant parties.
I run ubuntu’s server base headless install with a self-curated minimal set of gui packages on top of that (X11, awesome, pulse, thunar) but there’s no reason you couldn’t install kde with wayland. Building the system yourself gets you really far in the anti-bloatware dept, and the breadth of wiki/google/gpt based around Debian/Ubuntu means you can figure just about any issues out. I do this on a ~$200 eBay random old Dell + a 3050 6gb (slot power only).
For lighter gaming I’ll use the Ubuntu PC directly, but for anything heavier I have a win11 PC in the basement that has no other task than to pipe steam over sunshine/moonlight
It is the best of both worlds.


the best way to learn is by doing!


I just built my own automation around their official documentation; it’s fantastic.
https://www.wireguard.com/#conceptual-overview


vyatta and vyatta-based (edgerouter, etc) I would say are good enough for the average consumer. If we’re deep enough in the weeds to be arguing the pros and cons of wireguard raw vs talescale; I think we’re certainly passed accepting a budget consumer router as acceptably meeting these and other needs.
Also you don’t need port forwarding and ddns for internal routing. My phone and laptop both have automation in place for switching wireguard profiles based on network SSID. At home, all traffic is routed locally; outside of my network everything goes through ddns/port forwarding.
If you’re really paranoid about it, you could always skip the port-forward route, and set up a wireguard-based mesh yourself using an external vps as a relay. That way you don’t have to open anything directly, and internal traffic still routes when you don’t have an internet connection at home. It’s basically what talescale is, except in this case you control the keys and have better insight into who is using them, and you reverse the authentication paradigm from external to internal.


Talescale proper gives you an external dependency (and a lot of security risk), but the underlying technology (wireguard) does not have the same limitation. You should just deploy wireguard yourself; it’s not as scary as it sounds.
bill helped his brother jack, off a horse
bill helped his brother jack off a horse
Commas are important, who knew? If only he had paid attention in English class!