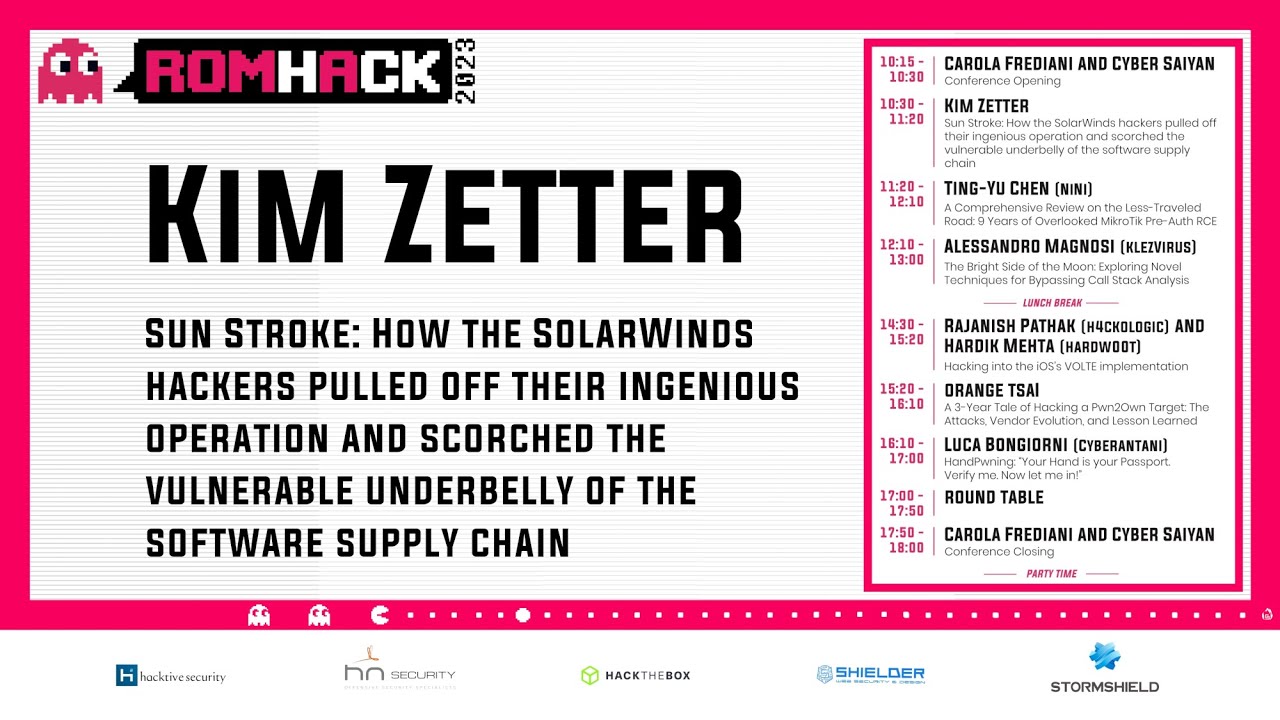
Kim Zetter
Sun Stroke: How the SolarWinds hackers pulled off their ingenious operation and scorched the vulnerable underbelly of the software supply chain
In November 2020 when a Mandiant analyst decided to investigate a routine security alert that many others would have ignored, she had no idea what her simple sleuthing would uncover — a massive espionage campaign that slipped past the protections of some of the most secure government agencies and tech titans in the world and exposed a major vulnerability at the core of the software supply chain. In a single ingenious stroke that should have surprised no one, the hackers hijacked the build server of a global software supplier and injected their code into a trusted update. With that one feat they managed to infect more than 16,000 customers across government and industry — from the Department of Homeland Security to Microsoft and Mandiant, from VPN suppliers to managed service providers — and remain undetected for nearly a year.
This keynote will examine how the Russian spies behind the operation pulled off their masterful hack and how they were ultimately caught after several near-misses. It will look at the mistakes that were made — on the part of the intruders, investigators, and victims — and what the operation taught us. And it will reveal what we still don’t know about the campaign.